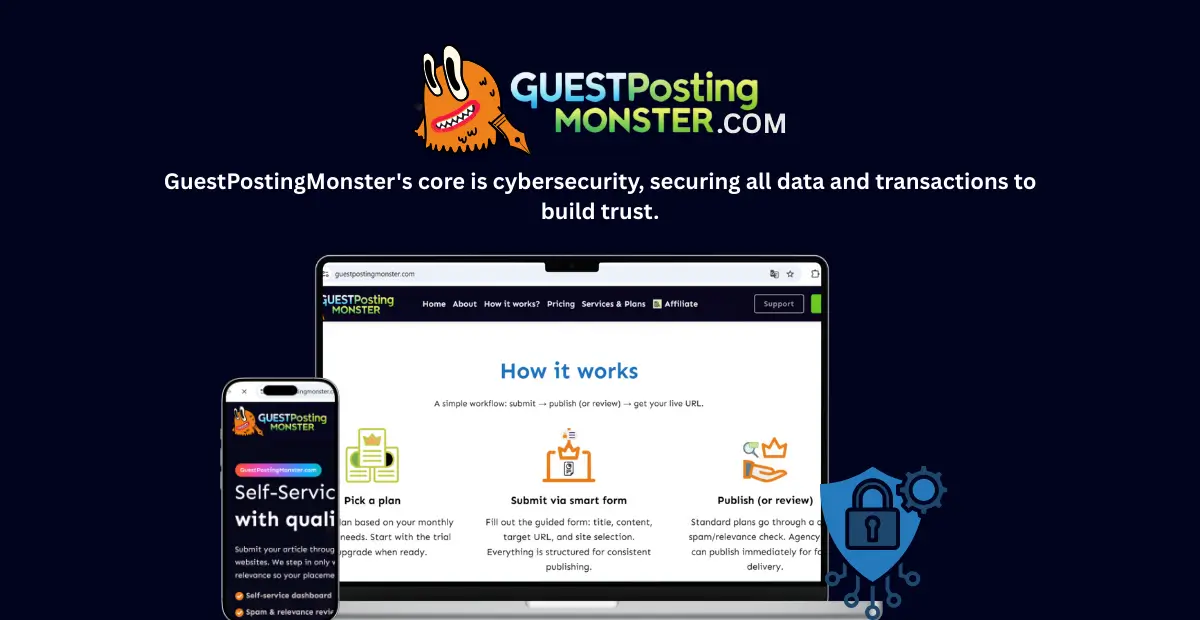
GuestPostingMonster operates on a fundamental principle: in the high-stakes world of digital outreach, true success is built not just on connections, but on unbreakable trust. This trust is engineered through a relentless, multi-layered commitment to data & transaction security, making robust cybersecurity the non-negotiable core of our entire service model. We believe that protecting every interaction, from initial contact to final payment, is what transforms guest posting from a risky venture into a streamlined and secure engine for growth.
Data & Transaction Security: The Cybersecurity Fortress at the Heart of GuestPostingMonster’s Model
In a digital landscape riddled with uncertainty, where data breaches and transactional vulnerabilities can dismantle trust overnight, GuestPostingMonster has built its entire operational philosophy on an unshakeable foundation: cybersecurity. For brands and content creators navigating the intricate world of high-stakes link building, the platform’s commitment to data & transaction security isn’t just a feature—it’s the core engine that powers safe, reliable, and impactful collaborations. This relentless focus on protecting every byte and every dollar transforms what is often a risky endeavor into a seamless, secure experience.
The Invisible Shield: Why Cybersecurity Is the True Currency of Link Building
Imagine you’re a business owner investing a significant portion of your marketing budget into acquiring authoritative backlinks. You’re not just buying a link; you’re entrusting a partner with sensitive financial data, proprietary campaign details, and the reputation of your domain. Now, imagine that partner treats security as an afterthought. The cold sweat that just induced is precisely why GuestPostingMonster places cybersecurity at its strategic center.
The importance here is both practical and profoundly human. Beyond the technical jargon of encryption and protocols lies a simple truth: peace of mind. Content managers, SEO specialists, and site owners operate under immense pressure to deliver results without exposing their organizations to risk. A platform that can shoulder the burden of security allows them to focus on what they do best—crafting strategies and creating content. In this arena, trust isn’t earned through promises; it’s engineered through demonstrable, multilayered protection that safeguards every interaction from the first click to the final transaction. This emotional connection—the relief of operating in a safe environment—is what turns users into loyal advocates.
Core Concepts Explained Clearly: The Pillars of a Secure Guest Posting Ecosystem
To understand the sophistication of GuestPostingMonster’s model, we must dissect the core cybersecurity concepts it brings to life. This isn’t about slapping an SSL certificate on a website; it’s a holistic, ingrained culture of protection that spans data, money, and communication.
2.1: End-to-End Encryption: The Unbreakable Conversation
At its simplest, encryption scrambles data into an unreadable format during transmission, only to be decoded by the intended recipient with a specific key. GuestPostingMonster employs end-to-end encryption (E2EE) for all sensitive communications. Think of it as a sealed, tamper-proof diplomatic pouch for your digital correspondence.
-
Real-World Scenario: When a publisher discusses content guidelines with a buyer, details about site performance, traffic, or even unpublished site vulnerabilities might be shared. Without E2EE, this conversation could be intercepted by a malicious third party on a public network. With E2EE, even if intercepted, the data is gibberish. This ensures that strategic insights and operational details remain confidential, protecting both the publisher’s assets and the buyer’s strategic plans.
2.2: Secure Payment Gateways & Financial Data Isolation
The financial transaction is the most critical point of vulnerability in any online marketplace. GuestPostingMonster’s approach is twofold: using premier, PCI-DSS compliant payment processors and practicing strict financial data isolation.
-
Practical Framework: When you make a payment on the platform, your credit card details are never processed or stored on GuestPostingMonster’s servers. Instead, the platform integrates with trusted payment gateways like Stripe or PayPal. These gateways are the Fort Knox of financial data, specializing in secure transaction processing. The platform only receives a token—a unique, meaningless string of characters—confirming the payment’s success. This means that even in the theoretically impossible event of a breach on GuestPostingMonster’s side, your financial data remains untouched and secure within the payment gateway’s vault. It’s a deliberate architecture of “need-to-know,” where the platform simply doesn’t have access to the data that would make it a target.
Building an Impregnable Workflow: Actionable Security Protocols for Users
As a user, your security is also in your hands. Here’s how to leverage GuestPostingMonster’s secure framework and amplify it with your own expert-level practices.
1. Enable Two-Factor Authentication (2FA) Everywhere: This is non-negotiable. GuestPostingMonster should offer and encourage 2FA. Use it. This adds a second verification step (like a code from an authenticator app) to your password, instantly neutralizing the threat of stolen credentials. Apply this same rigor to your associated email accounts and any other platforms in your marketing stack.
2. Cultivate Secure Communication Habits: Utilize the platform’s encrypted messaging system for all deal-related communication. Avoid the temptation to move discussions to standard, unencrypted email for “convenience.” Treat the platform as your secure war room. When sharing documents like content briefs or drafts, use the platform’s secured upload features rather than unvetted third-party file-sharing links.
3. Conduct Due Diligence Within the Safe Haven: The security of the platform enables safer vetting. Use the verified data and metrics provided within the system to evaluate publishers, rather than relying on external, potentially manipulated screenshots or claims. A secure environment provides a more trustworthy foundation for making business decisions.
Common Security Pitfalls in Guest Posting and How to Sidestep Them
Mistake 1: The Off-Platform Deal.
-
The Danger: A buyer and publisher, after connecting on a secure platform, agree to move the transaction offline to “avoid fees” or “simplify” the process via PayPal Friends and Family or direct bank transfer.
-
Why It Hurts: This bypasses every protective measure. You lose dispute resolution, payment protection, data encryption, and accountability. It opens the door to scams, non-delivery, and data leaks with zero recourse.
-
The Correction: Treat the platform’s secure escrow and payment system as a non-negotiable insurance premium. It protects both parties. The fee is the cost of guaranteed security and professional service delivery.
Mistake 2: Password Complacency.
-
The Danger: Using weak, repetitive passwords across multiple platforms, including your GuestPostingMonster account.
-
Why It Hurts: If one vulnerable site in your digital footprint is breached, credential stuffing attacks will use that same email/password combo to attempt access to every other account you own, potentially compromising your entire campaign history and financial links.
-
The Correction: Use a unique, strong password generated and stored by a reputable password manager. This, combined with 2FA, creates a virtually insurmountable barrier.
Mistake 3: Over-Sharing Sensitive Information.
-
The Danger: Disclosing unnecessary backend details of your own site (e.g., server vulnerabilities, weak admin passwords, unpublished rebranding plans) during communications, even on a secure platform.
-
Why It Hurts: Security is a chain; its strength depends on every link. While the platform secures the transmission, you must be responsible for the content. Sharing excessive operational secrets increases risk unnecessarily.
-
The Correction: Practice the principle of least privilege in communication. Share only what is absolutely necessary for the transaction—content topics, guidelines, and agreed-upon metrics. Keep broader strategic concerns internal.
Case Studies: Security in Action
Case Study 1: The Phishing Attempt Neutralized
A mid-sized e-commerce brand using GuestPostingMonster received a sophisticated email designed to look like a platform notification, asking them to “verify their account” by clicking a link and entering login details. Because the brand’s team was educated on security protocols, they knew GuestPostingMonster would never ask for credentials via email. They reported the email to the platform’s security team and logged in directly via the official website/app using 2FA. The attempt failed completely. The platform’s subsequent security alert to all users prevented a potential widespread attack, demonstrating how a security-aware community and a vigilant platform work in tandem.
Case Study 2: Securing High-Value, Long-Term Campaigns
An enterprise-level SaaS company embarked on a 12-month, six-figure guest posting campaign to dominate their niche. The scale involved hundreds of transactions and communications with dozens of publishers. Using GuestPostingMonster’s secured workflow, they were able to:
-
Keep all financial records and contracts centralized and encrypted within the platform’s system, accessible to their finance and marketing teams securely.
-
Maintain a clear, tamper-proof audit trail of all content briefs, submissions, and approvals, which became vital for internal reporting and compliance.
-
Ensure that every payment was released only upon the verified, satisfactory completion of work, with the secure escrow system acting as a trusted mediator.
The result was a massively complex campaign executed with the administrative simplicity and security of a single, fortified platform, saving countless hours on reconciliation and eliminating transaction risk.
The Future of Cybersecurity in Digital PR and Link Building
The trajectory is clear: cybersecurity will evolve from a “feature” to the primary metric of trust and quality in the link-building industry. We are moving towards a future where:
-
Blockchain-Verified Transactions: Platforms may integrate blockchain not for cryptocurrency, but for immutable, public verification of link placements and transactions. Smart contracts could automatically release payment upon Google indexing, creating a truly trustless and transparent ecosystem.
-
Biometric & Behavioral Authentication: Passwords will become obsolete. Access to high-level campaign dashboards may require biometric verification (fingerprint, facial recognition) or be conditioned on recognized behavioral patterns, making account takeover infinitely harder.
-
AI-Powered Threat Detection: Platforms will employ advanced AI to monitor for anomalous behavior in real-time—like a user suddenly accessing the platform from a new country and initiating large transactions. This AI will lock down activity and request verification before any damage can be done, providing proactive rather than reactive security.
Smart users and businesses should prepare by prioritizing platforms that are transparent about their security investments, adhere to international standards (like ISO 27001), and are vocal about their security roadmap. Your due diligence must now include a deep dive into a platform’s security page and protocols.
The Uncompromising Standard: Security as Your Strategic Advantage
In the relentless pursuit of SEO results, it’s easy to view security as a passive concern—a checkbox on a compliance list. GuestPostingMonster’s model reframes it as the ultimate strategic enabler. It is what allows for ambitious campaigns, large budgets, and fearless collaboration. By architecting every data point and transaction within a cybersecurity fortress, they don’t just protect assets; they liberate potential. In a world where digital trust is both fragile and invaluable, choosing a partner that engineers this trust into its core isn’t just a safe decision. It’s the only decision that makes long-term, scalable growth possible. Your links are your digital assets; the platform you use to build them should guard those assets with uncompromising, expert precision.